
From the server administrators of highly technological organizations, to product managers of financial institutions, down to the one-man startups that just want to secure their shopping cart, the same question pops up: “If TLS/SSL certificates all do the same thing, what type should we get?”
All three types of TLS/SSL certificates do fundamentally the same thing: encrypt information during TLS negotiations. Correctly installed and configured, both https and the padlock will show in most browsers.
However, beyond the padlock there are varying levels of security and risk.
What type of TLS/SSL certificate should you get?
Most security administrators have done their homework on the technical specifications before requesting a certificate. Is it for internal or public use? What is the user base and their method of use? What operating system and server software are involved? What systems will be impacted? What are the security policy requirements?
But beyond that, an TLS certificate is not just about the functionality or the key size, but about trust.
Consumer Awareness
Research shows that as online fraud grows, consumer digital trust in organization declines. With consumer-facing sites, you want to gain trust. So keep in mind your users’ trust and what you convey to them about your organization as you choose a TLS certificate.
Types of TLS/SSL certificates
There are three types of TLS certificates: Domain Validation (DV), Organization Validation (OV) and Extended Validation (EV). Certificate authorities (CAs), like DigiCert, validate each type of certificate to a different level of user trust.
Domain Validation Certificate
Domain Validated certificates are checked against a domain registry to prove ownership of the site domain. However, DV certificates do not offer identifying organizational information. So it is not recommended to use DV certificates for commercial purposes. They may be the cheapest type of certificate to get, but they provide no authentication value in terms of who is behind the website.
Site visitors cannot validate if the business identity is legitimate via the certificate, leaving them more exposed to online fraud. Accordingly, DV certificates should be used only where authentication is not a concern, such as protected internal systems.
An example of a DV certificate in Chrome (after clicking on the padlock):
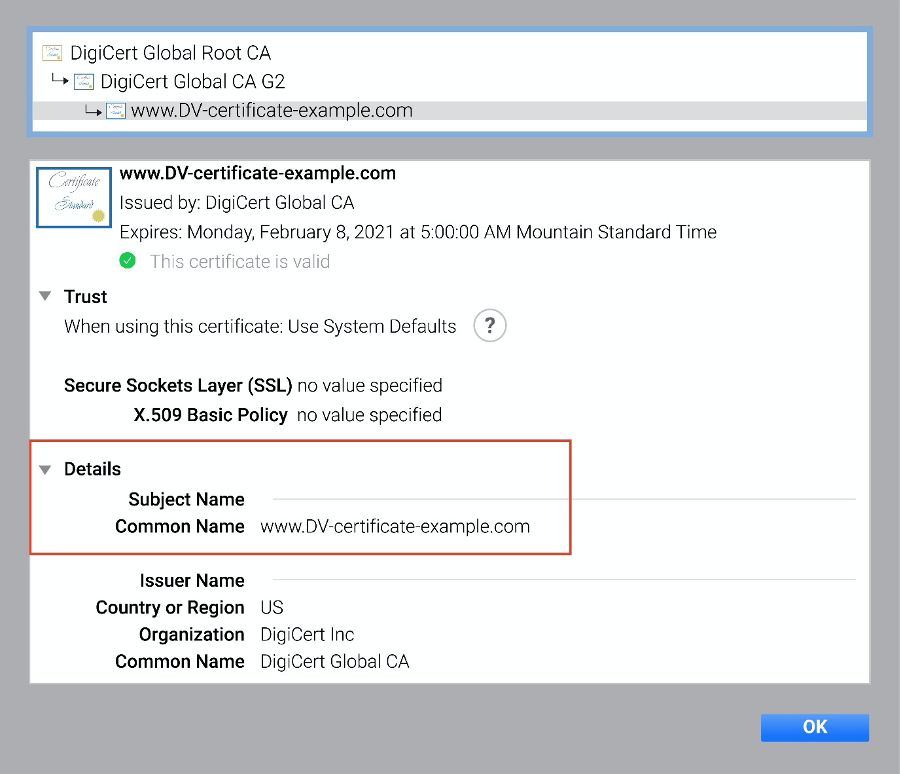
Note that only the common name, or domain, is verified.
Organization Validation Certificate
To receive an OV certificate, organizations are authenticated by the CA against business registry databases hosted by governments. CAs may require certain documents and contact personnel to ensure that OV certificates contain legitimate business information. This is the standard type of certificate required on a commercial or public-facing website.
An example of an OV certificate in Chrome (after clicking on the padlock):
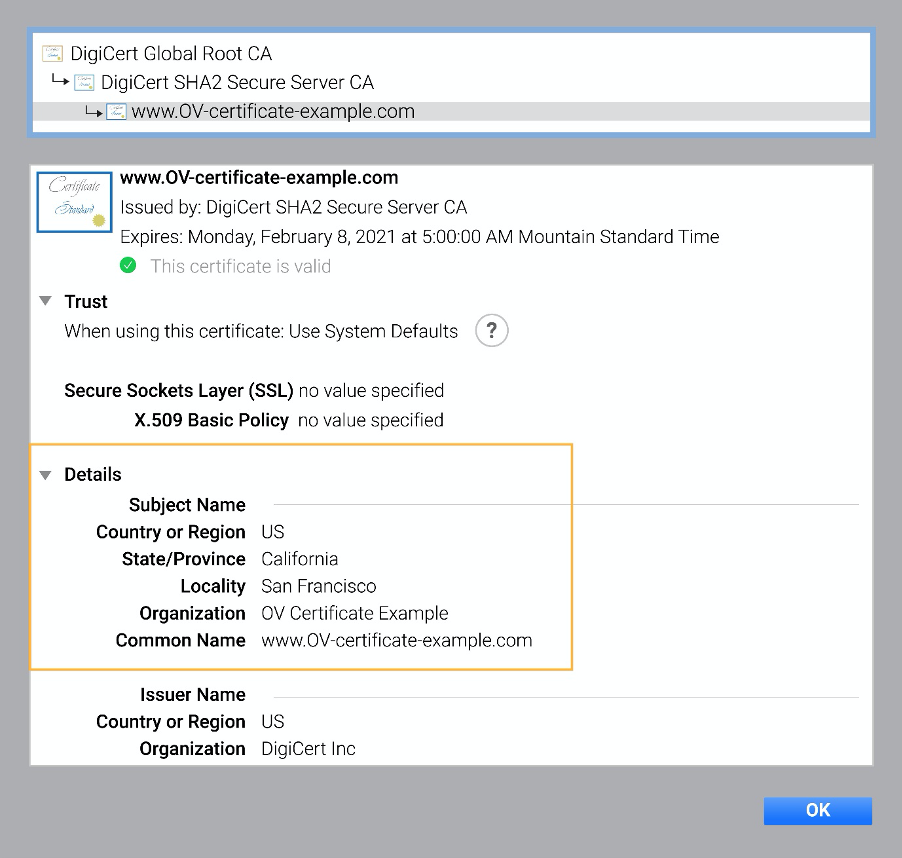
With OV not only is the common name verified but also the country, state, city and organization.
Extended Validation Certificate
EV certificates add additional validation steps and offer the highest level of authentication to safeguard your brand and protect your users. While not every site on the web uses EV certificates, they are used by the world’s leading organizations to ensure user trust. Over half of the top 400 ecommerce sites use EV, according to 2019 data from Comscore and Netcraft. They have found that switching from OV to EV certificates increases online transactions and improves customer confidence.
But they are not just for ecommerce: EV certificates give your brand the highest level of assurance and validation to ensure users know exactly where — and to whom — encrypted data is being sent. That’s why EV is the global industry standard for encrypting highly sensitive data. EV certificates are used for account area logins, front-facing webpages and other sensitive areas.
Plus, it is extremely difficult to impersonate an EV-enabled site. Websites using EV certificates have virtually zero incidents of identity-spoofing attacks. This is significant because $17,700 is lost every minute due to phishing attacks. Phishing attacks account for more than 80 percent of reported security incidents.
Below is an example of an EV certificate in Chrome (see examples of what EV certificates look like in each browser). Note that an EV certificate in Chrome will say "Certificate Valid, Issued to: Name of Company (US)". If you want more details, you can click on “Certificate” for more information.
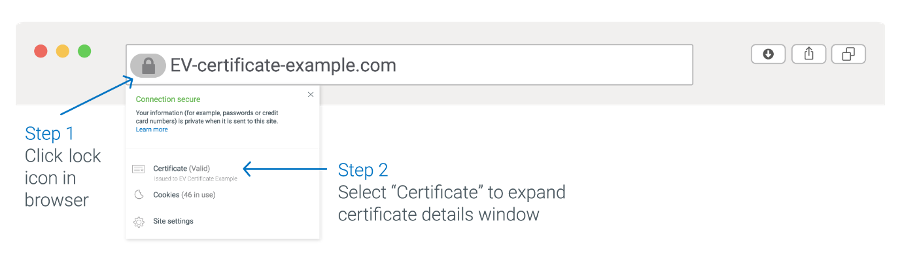
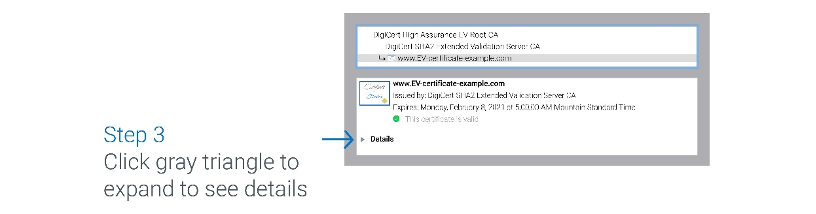
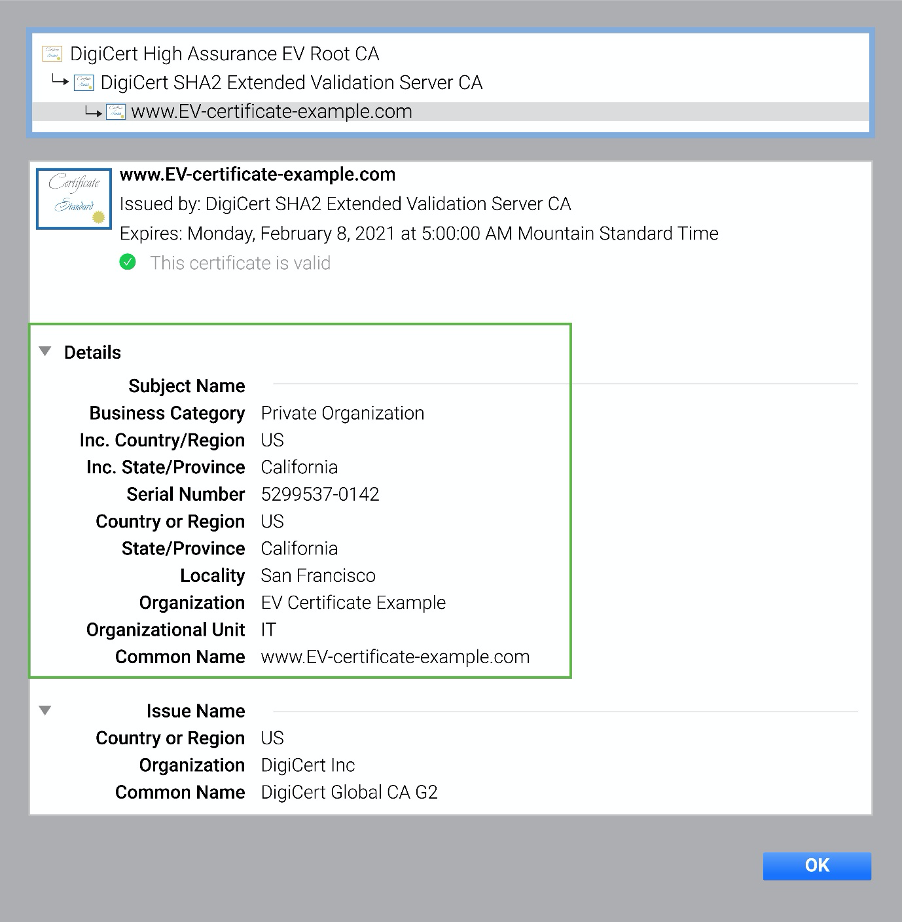
EV certificates show all the details of OV and DV plus additional identifying information.
Go beyond security with EV
Extended Validation goes beyond security. It has become the baseline for any reputable site that cares about security, brand and their clients. EV makes a strong statement that your brand is committed to data security and offers the highest level of protection for your users.
Once you’ve chosen your certificate type, here’s how to get it installed.













